Email Security Best Practices for Small Businesses in 2026

Email Security Best Practices for Small Businesses in 2026 Email remains the most common entry point for cyber attacks against small businesses. Phishing, account takeovers, and malware delivered through email continue to cause downtime, data loss, and financial damage. The problem is not that email technology is unsafe. The problem is that email is often […]
How Small Businesses Can Prevent Ransomware Without Enterprise Budgets

How Small Businesses Can Prevent Ransomware Without Enterprise Budgets Ransomware is no longer a problem reserved for large organizations. Small businesses are now one of the most common targets because attackers know many lack consistent security protections. The good news is that preventing ransomware does not require expensive enterprise tools or a full time security […]
What Managed IT Services Actually Include A Simple Guide for Business Owners

What Managed IT Services Actually Include A Simple Guide for Business Owners Many small business owners know they need IT help, but are not always sure what managed IT services actually include. For some, IT support still means calling someone only when something breaks. For others, it feels like a monthly cost without clear value. […]
Why Every Small Business Needs a Modern Backup Strategy

Why Every Small Business Needs a Modern Backup Strategy Most small businesses believe they are backed up. Unfortunately, many only find out the truth when something goes wrong. A server crashes. A file gets deleted. A ransomware attack locks everything. Suddenly the question is no longer whether backups exist, but whether they actually work. In […]
The Essential 2026 Cybersecurity Checklist for Small Businesses

The Essential 2026 Cybersecurity Checklist for Small Businesses Cybersecurity in 2026 looks very different than it did just a few years ago. Unfortunately, one thing has not changed. Small businesses are still one of the most common targets for cyber attacks. This is not because attackers are singling out small companies. It is because many […]
Top IT Challenges Small Businesses Face (And How to Fix Them)

Running a small business is hard enough without technology slowing you down. But let’s be honest… most small businesses aren’t running fancy enterprise systems. They’re working with a mix of older computers, aging WiFi routers, and whatever setup “worked fine at the time.” There’s no shame in that. Small businesses hustle. You prioritize customers, payroll, […]
7 Expert Tech Tips for Small Business Success in 2025

7 Expert Tech Tips for Small Business Success in 2025 Running a small business in today’s digital-first environment can feel overwhelming. With technology evolving at breakneck speed, staying ahead requires more than just keeping the lights on. It requires smart decisions and strategic implementation of the right tools. Here are seven expert tech tips every […]
Why It’s Time to Move from IMAP Email to Microsoft 365
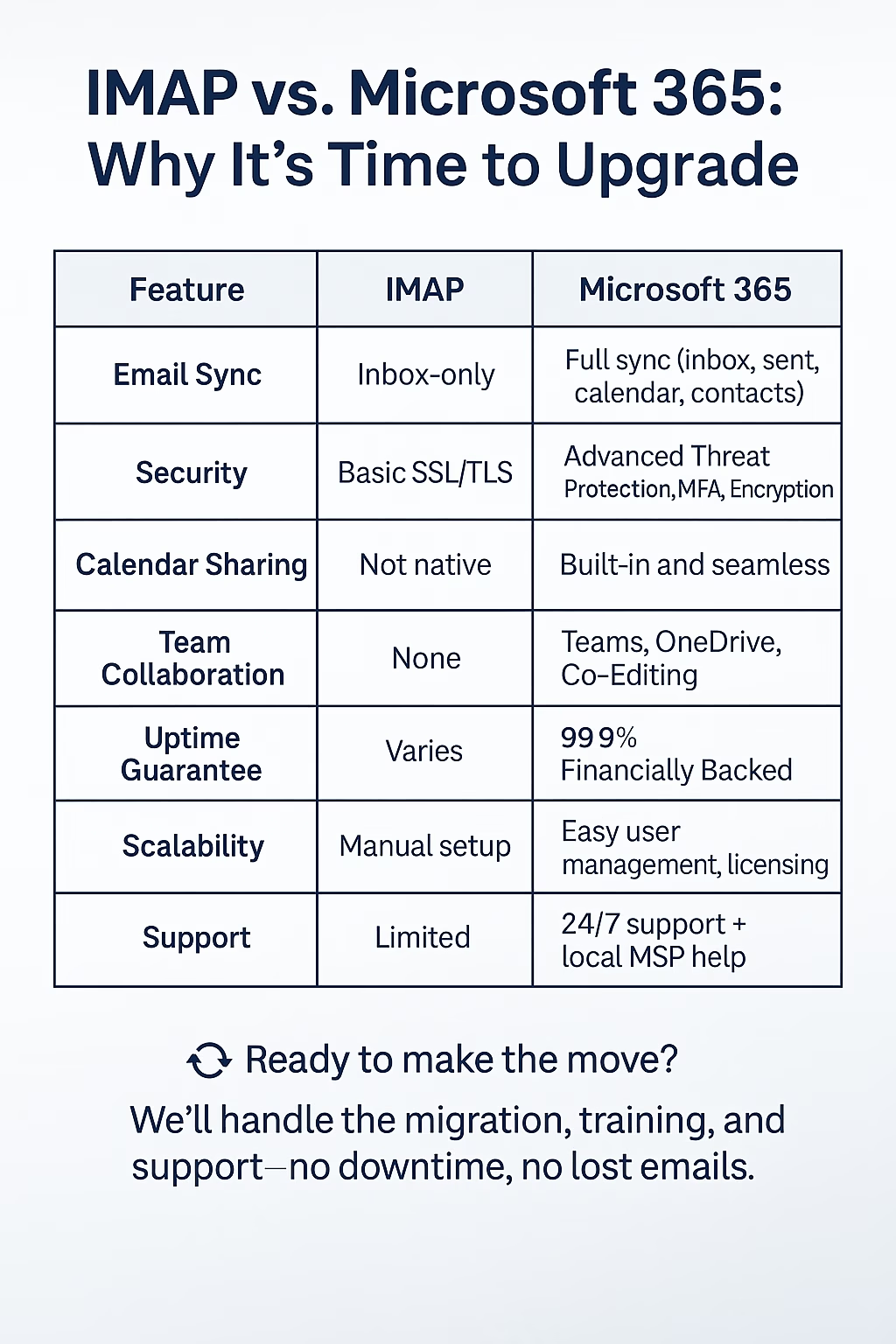
If you’re still using a basic IMAP email setup for your business, it’s time to seriously consider making a change. While IMAP might seem “good enough,” it’s outdated, limited, and lacking modern features. Enter Microsoft 365—a secure, cloud-based platform that does far more than just email. Whether you’re a growing team or need a secure […]
7 Signs Your Business Has Outgrown Basic IMAP Email

If you’re still relying on a basic IMAP email service, your business could be exposed to security risks you don’t even see coming. IMAP might be familiar and simple, but it’s no longer fit for modern business communication—especially when it comes to protecting sensitive data and ensuring email compliance. Here are 7 warning signs it’s […]
Why Restarting Your Computer Fixes So Many Issues

Why Restarting Your Computer Actually Fixes Things We’ve all been there: your computer is running slow, your apps aren’t responding, or something just feels… off. The advice you hear over and over again — “Try turning it off and back on again” — might sound like a tech support cliché, but there’s a very real […]
