How to Train Employees to Avoid IT Security Mistakes
Introduction
In an era where cyber threats evolve faster than ever, businesses must address the single biggest vulnerability in their IT systems: their people. Studies from the World Economic Forum and IBM consistently show that human error accounts for over 90% of data breaches. From unintentional email disclosures to falling for fake login pages, employees are frequently targeted as the weakest link.
Yet, they can also become your first line of defense. Investing in regular, targeted employee cybersecurity training helps create a resilient security culture—one that minimizes costly mistakes and reinforces trust between your business and its clients. For more on how we help organizations protect their systems, visit our Cybersecurity Services page.
Understanding the Human Factor in Cybersecurity
Despite the increasing complexity of cyberattacks, many breaches start with simple mistakes—like clicking a malicious link or reusing a password. According to Verizon’s Data Breach Investigations Report (DBIR), over 80% of breaches involve human error or social engineering. These aren’t just tech problems—they’re behavioral ones.
The National Institute of Standards and Technology (NIST) emphasizes that cybersecurity programs must be built around people, not just tools. Employees need to understand not just the “what” but the “why” behind secure practices. For instance, explaining how phishing works and how attackers mimic familiar vendors or colleagues gives people practical context. When users understand the real-world tactics of cybercriminals, they’re more likely to question suspicious emails or links instead of blindly clicking.
Identifying the Most Common IT Security Mistakes Employees Make
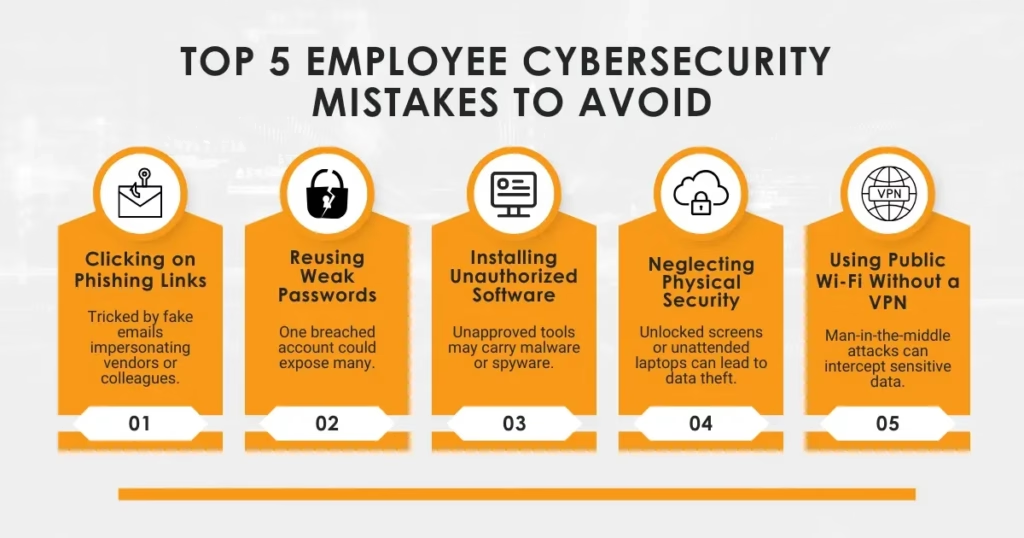
- Clicking on Phishing Links: Phishing emails are designed to impersonate legitimate contacts. Employees might be tricked into giving away login credentials, wire transfer approvals, or sensitive files. Many attackers use urgency (“Update now!” or “Your account is locked!”) to exploit quick decision-making.
- Using Weak or Reused Passwords: Despite the rise of MFA, weak passwords remain a top risk. Reused passwords across platforms can expose corporate accounts after just one breach—often sourced from data dumps on the dark web.
- Installing Unauthorized Software: Known as “shadow IT,” employees often download tools or apps without IT approval. These downloads could contain malware, spyware, or vulnerabilities that compromise company networks.
- Neglecting Physical Security: Leaving a laptop in a coffee shop or forgetting to lock a screen are simple mistakes with serious consequences. Insider threats also come from unauthorized physical access to unattended devices.
- Using Unsecured Wi-Fi: Public networks like those in airports or cafes can be spoofed. Without a VPN, employees working remotely could expose credentials or sensitive files to man-in-the-middle attacks.
The Psychology of Employee Mistakes: Why They Happen
It’s easy to assume that employees who make security mistakes are careless—but it’s rarely that simple. Behavioral science tells us that under pressure, people default to habits—not protocols. In one study by Stanford University, 88% of data breach incidents were caused by employee mistakes due to stress, distraction, or lack of understanding.
Employees are often juggling competing priorities, which can result in skipping steps like checking email sources or verifying file downloads. Security training should acknowledge these psychological realities. Rather than blaming users, it should empower them through relatable scenarios, real-life examples, and role-based learning that makes training feel relevant instead of redundant.
Building a Cybersecurity-First Workplace Culture
Culture is a stronger security tool than any firewall. When cybersecurity becomes a daily part of your company culture, it’s no longer seen as a box to check—but as a shared mission. This mindset shift transforms employees from liabilities into assets.
Create environments where asking questions is encouraged. If an employee is unsure about an email attachment, they should feel empowered to report it—without fear of being blamed if it turns out to be benign. Security becomes everyone’s job, and collective vigilance grows.
Leadership buy-in is critical. When executives participate in training and communicate the importance of cyber hygiene, it sends a clear message across all departments. Incentivize best practices with gamified rewards, peer recognition, or even small bonuses for catching phishing simulations.
Designing Effective Cybersecurity Training Programs
The best training programs are continuous, engaging, and contextual. That means ditching the once-a-year PowerPoint slides in favor of modular, interactive sessions that reflect real threats. Here’s how to elevate your program:
- Interactive Modules: Quizzes, mini-games, or real-time decision-making simulations (e.g., “Would you click this?”)
- Role-Based Scenarios: Tailor lessons to HR, finance, IT, and C-level roles
- Live Phishing Tests: Use internal simulations to measure reflexes under pressure
- Mobile Access: Allow access on smartphones so learning happens on the go
Reviewing employee performance after each module helps refine the content and identify training gaps.
What to Include in Your Training Curriculum
- Email and Phishing Awareness – Teach how to inspect email headers, recognize spoofed domains, and handle attachments safely
- Password and MFA Best Practices – Encourage strong passwords and provide secure password managers
- Safe Remote Work – Train staff to use VPNs, secure cloud services, and avoid using personal devices for work data
- Device Security – Emphasize physical safeguards like auto-locks, encrypted drives, and locking screens
- Regulatory Compliance – Tailor content to your industry’s requirements: HIPAA, GDPR, PCI-DSS, etc.
Role-Based Training Strategies
A finance employee has different cybersecurity concerns than a marketing intern. Personalizing training to each role makes it more effective:
- Finance: Business email compromise, invoice fraud, and wire transfer verification
- HR: Securing employee records and safe onboarding/offboarding protocols
- IT/Developers: Secure coding, credential management, and server access security
- Executives: High-level social engineering awareness and communication hygiene
Microlearning and Ongoing Education
Cybersecurity knowledge fades fast. Microlearning delivers small, targeted lessons that keep knowledge fresh without overwhelming staff. Examples include:
- Weekly “Security Tips” email series
- Two-minute video refreshers on spotting phishing emails
- Monthly simulated phishing campaigns with analytics
By integrating microlearning into your workflow, you sustain awareness throughout the year.
Tools That Help Employees Stay Secure
- Password Managers (e.g., Bitwarden, LastPass) – Encourage safe credential handling
- <strongVPNs – Protect remote connections from prying eyes
- Multi-Factor Authentication (MFA) – Require this for logins, especially for admin access
- Endpoint Protection Software – Use EDR platforms to alert unusual device activity
Make training for these tools part of onboarding. Too many security tools go unused simply because employees don’t know how to use them confidently.
Monitoring and Measuring Training Effectiveness
What gets measured gets improved. Use these KPIs to track progress:
- Click-through rates on phishing simulations
- Training completion and quiz scores
- Number of user-reported phishing attempts
- Time-to-report metrics for actual incidents
Use this data to fine-tune your strategy and identify departments that need more attention or different methods.
Avoiding Common Pitfalls in Employee Training
Don’t let your training efforts fall short by making these mistakes:
- 💡 Overloading users: Too much content at once leads to burnout and poor retention
- 💡 Outdated examples: Use current threats—don’t teach phishing with decade-old screenshots
- 💡 Ignoring feedback: Listen to what learners say and adapt your content
How Managed IT Services Can Support Your Training Goals
Cybersecurity training can’t be an afterthought—it’s a strategic imperative. Managed service providers like Advanced IT Support help organizations build robust, adaptive training programs backed by expert support, real-time monitoring, and ongoing policy updates. We help take the guesswork out of cybersecurity education and integrate it with your broader IT infrastructure.
Conclusion: Empowering Employees as the First Line of Defense
When it comes to protecting your digital assets, technology is only half the equation—people are the other. By equipping your employees with the knowledge, tools, and confidence to act securely, you turn them into your strongest line of defense.
Security doesn’t happen in a vacuum. It’s a culture, a strategy, and a commitment to smarter business practices. Want help implementing a scalable training program or tightening your endpoint protections? Explore our IT Support Services to start building a safer, smarter business environment today.
FAQs
- How often should companies update cybersecurity training?
At least every six months, with microlearning content monthly. Update sooner if new threats emerge. - What are the signs of effective training?
Improved phishing test scores, increased incident reporting, and higher employee engagement. - Should cybersecurity training be mandatory?
Yes. Every employee, from interns to C-level execs, must be trained regularly. - Can small businesses afford high-quality training?
Absolutely. Affordable SaaS platforms and managed service packages are available even for small teams. - What’s the best way to measure employee progress?
Use LMS analytics, phishing simulation results, and survey-based knowledge checks to track learning.
